Cryptography Trends 2025: Navigating A Quantum-Resistant Future
Cryptography Trends 2025: Navigating a Quantum-Resistant Future
The landscape of cryptography is constantly evolving, driven by the relentless march of technology and the ever-present threat of evolving cyberattacks. As we stand on the precipice of 2025, several key trends are shaping the future of this vital field, promising both unprecedented security and complex challenges.
1. The Quantum Threat: Embracing Post-Quantum Cryptography
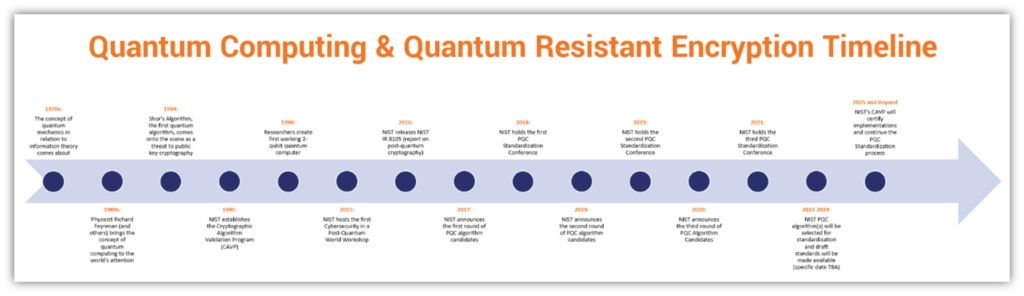
The emergence of quantum computers poses a significant threat to classical cryptography. Quantum algorithms like Shor’s algorithm can break widely used encryption methods, including RSA and ECC, rendering our current security infrastructure vulnerable. This looming threat has spurred the development of Post-Quantum Cryptography (PQC), a new generation of algorithms resistant to quantum attacks.
The PQC Landscape:
- NIST Standardization: The National Institute of Standards and Technology (NIST) is leading the charge in standardizing PQC algorithms. The ongoing process involves rigorous analysis and evaluation of candidate algorithms, with several finalists vying for official recognition.
- Implementation Challenges: Integrating PQC into existing systems presents significant challenges. The new algorithms are often computationally more intensive, requiring adaptation of hardware and software infrastructure.
- Hybrid Approaches: Combining classical and PQC techniques offers a viable strategy for securing systems against both present and future threats. This approach involves using PQC for long-term security and leveraging classical cryptography for performance optimization.
2. The Rise of Homomorphic Encryption:
Homomorphic encryption (HE) is a revolutionary technology that allows computations to be performed on encrypted data without decrypting it. This capability opens up exciting possibilities for privacy-preserving data analysis, secure cloud computing, and secure machine learning.
HE’s Impact:
- Data Privacy and Security: HE enables sensitive data to be processed without compromising its confidentiality. This is crucial for protecting personal information, medical records, and financial transactions.
- Secure Cloud Computing: HE allows for secure computation on data stored in the cloud, eliminating the need to trust third-party providers with sensitive information.
- Privacy-Preserving Machine Learning: HE empowers the development of machine learning models that can be trained and deployed without compromising the privacy of the training data.
3. The Importance of Secure Communication:
The increasing reliance on digital communication and the proliferation of connected devices demand robust security measures. Cryptography plays a crucial role in ensuring secure communication channels, safeguarding data from unauthorized access and manipulation.
Secure Communication Trends:
- End-to-End Encryption: This technique ensures that only the intended sender and receiver can access the message content, providing the highest level of security.
- Zero-Trust Security: This approach assumes that no user or device can be trusted by default, requiring strict authentication and authorization protocols for accessing resources.
- Secure Messaging Protocols: Secure messaging apps like Signal and WhatsApp employ end-to-end encryption and other cryptographic techniques to protect user privacy.
4. The Evolution of Blockchain and Cryptocurrencies:
Blockchain technology, underpinning cryptocurrencies like Bitcoin and Ethereum, relies heavily on cryptography for its security and integrity. The ongoing development of blockchain applications and the emergence of new cryptocurrencies are driving innovation in cryptographic techniques.
Cryptographic Innovations in Blockchain:
- Consensus Mechanisms: Cryptographic algorithms are used to ensure consensus among network participants, validating transactions and maintaining the integrity of the blockchain.
- Smart Contracts: These self-executing contracts leverage cryptography to automate agreements and enforce terms, eliminating the need for intermediaries.
- Privacy-Enhancing Technologies: Techniques like zero-knowledge proofs and homomorphic encryption are being explored to enhance the privacy of blockchain transactions.
5. The Growing Role of Cryptography in AI and Machine Learning:
The integration of cryptography with artificial intelligence (AI) and machine learning (ML) is paving the way for secure and privacy-preserving applications. Cryptographic techniques are used to protect sensitive data, ensure the integrity of AI models, and enable secure collaboration in AI development.
Cryptography in AI/ML:
- Secure AI Training: Cryptography can protect training data from unauthorized access, ensuring privacy while enabling the development of accurate AI models.
- Secure Inference: Cryptographic techniques can be used to perform inferences on encrypted data, enabling secure deployment of AI models in privacy-sensitive environments.
- Federated Learning: Cryptography plays a crucial role in federated learning, enabling collaborative model training without sharing raw data among participating devices.
6. The Importance of Cryptographic Agility:
The ever-changing threat landscape necessitates a flexible and agile approach to cryptography. Organizations need to adopt strategies that allow them to adapt to new threats and vulnerabilities quickly.
Cryptographic Agility Strategies:
- Regular Security Audits: Conducting regular security audits helps identify potential vulnerabilities and ensure that cryptographic implementations remain robust.
- Continuous Monitoring: Monitoring for emerging threats and vulnerabilities is crucial for staying ahead of attackers and implementing timely security updates.
- Flexible Cryptographic Frameworks: Adopting cryptographic frameworks that allow for easy integration of new algorithms and protocols ensures adaptability to evolving threats.
Challenges and Opportunities:
While these trends offer exciting opportunities for enhanced security and innovation, they also present challenges:
- Technical Complexity: Implementing and managing advanced cryptographic solutions requires specialized expertise and resources.
- Interoperability Issues: Ensuring interoperability between different cryptographic systems is crucial for seamless communication and collaboration.
- Cost and Performance Trade-offs: Implementing PQC and HE can be computationally intensive, potentially impacting performance and cost.
- Regulation and Compliance: Navigating the evolving regulatory landscape and ensuring compliance with data privacy laws is essential.
Conclusion:
Cryptography is no longer a niche technology; it is a cornerstone of modern society, underpinning our digital infrastructure, protecting our privacy, and enabling secure communication. As we navigate the challenges and embrace the opportunities of the future, it is essential to invest in robust cryptographic solutions, foster collaboration among experts, and promote awareness of the importance of cryptography in safeguarding our digital world. By staying vigilant, embracing innovation, and prioritizing security, we can build a more secure and trustworthy digital future.